Introduction
SAP Analytics Cloud (SAC) supports Direct Live Connection and Tunnel Live connection to On-Premise S/4HANA. Direct Live Connection is based on CORS and Tunnel Live Connection is based on SAP Cloud Connector. This blog explains the steps to establish Single Sign-On (SSO) using tunnel live connection to On-Premise S/4HANA.
This blog and configuration process is quite a lengthy one. It is requested for readers to not skip any of the sections and would suggest following the same sequence to avoid configuration errors.
Prerequisites
- SAP Analytics Cloud (SAC)
- SAP S/4HANA On-Premise
- SAML Identity Provider
- SAP Cloud Connector (SCC)
- SAP Web-Dispatcher (Optional)
Content
- Integration Architecture
- Overview of SSO using Principle Propagation
- Configure SAC to SCC
- Configure S/4HANA to SCC
- Principal Propagation Configuration in SCC
- Configure Certificates in SCC for Principal Propagation
- Setup Trust Between SCC and Web Dispatcher
- Setup Trust Between SCC and S/4HANA
- Configure Tunnel Live Connection in SAP Analytics Cloud
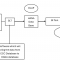
Integration Architecture
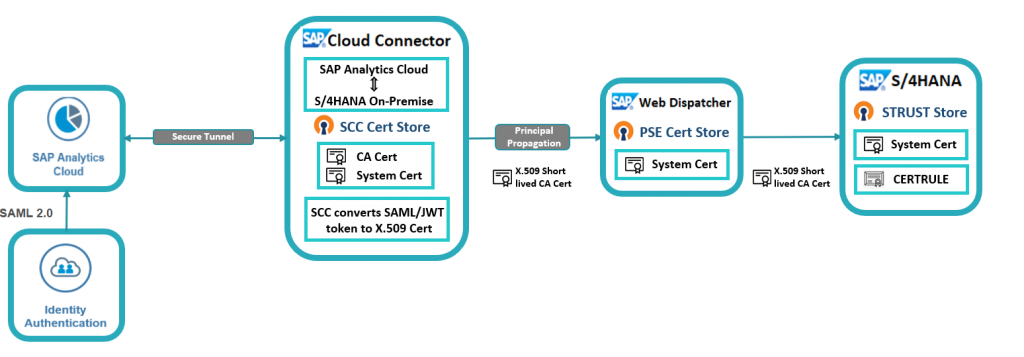
Overview of SSO Using Principal Propagation
The SSO in tunnel live connection between SAC and S/4HANA is based on Principle Propagation. In Principal Propagation, the provider dynamically generates a short-lived certificate for a user who has been authenticated to SAP Analytics Cloud by an identity provider.
Please find below the details of the request flow from SAC to S/4HANA.
The SAP Analytics Cloud is configured with SAML based identity provider for user authentication. In order to configure Tunnel based live connection with SSO to the backend system, the identity provider and identifier used for the SAC and backend S/4HANA system should be the same.
1) When users access an SAC dashboard, SAC establishes an https tunnel based connection to the backend S/4HANA using SAP Cloud Connector (SCC).
2) The SAP Cloud Connector receives the request from SAC along with a SAML/JWT token from the Cloud Foundry environment.
3) SCC generates a short-lived X.509 client certificate based on the SAML/JWT token.
4) The conversion from SAML/JWT to X.509 certificate only preserves the principal information, other SAML attributes will not be propagated to backend.
5) This short-lived X.509 certificate is propagated to the backend to establish SSO between SAC and S/4HANA.
6) This principle propagation configuration can be classified as two segments:
Configure SSL handshake: The two communication partners establish (mutual) trust between each other by exchanging certificates to establish an encrypted connection.
Configure user authentication: Where backend S/4HANA server validates and authenticates user requests based on the identifier coming from the client and then creates a user session for that particular user.
Step 1: Configure SAC to SCC
Connecting SAP Analytics Cloud to SAP Cloud Connector is based on the Data Centre of SAP Analytics Cloud tenant. When the SAC tenant is hosted on an SAP Data Centre (NEO), the region in SAC URL will have a single digit (e.g. org-sac.us1.hcs.cloud.sap) and if the SAC tenant is hosted on a non-SAP Data Centre (Cloud Foundry), the region in SAC URL will have two digits (e.g. org-sac.us10.hcs.cloud.sap).
1.1) Login to SAP Analytics Cloud.
1.2) In SAC Main Menu, Navigate to System > Administration.
1.3) Click Data source Configuration.
1.4) To edit the changes, click the Pencil Icon.
1.5) Add the S-User if the SAC tenant is hosted on SAP Data Centre (NEO).
1.6) Add the email address associated with the S-User, if the SAC tenant is hosted on Non-SAP Data Centre (Cloud Foundry).
1.7) Click Add S-User or Add Cloud Platform User button.
1.8) When clicking the Save button, the changes reflected should match the below screen shot:

1.9) Login to SAP Cloud Connector (SCC Url – https://:8443).
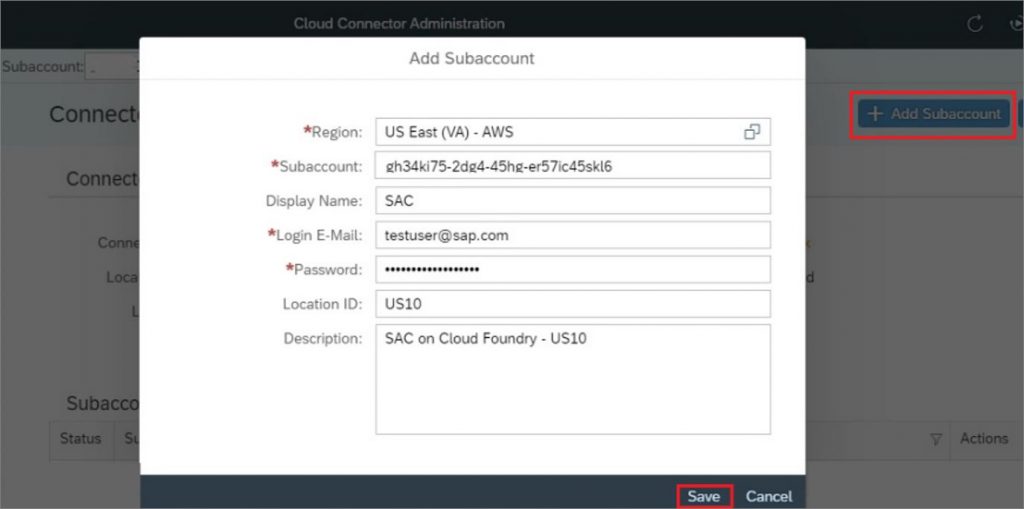
1.10) Click Add Subaccount button on the home screen.
1.11) Enter the SAC Data Centre region, name of SAC subaccount.
1.12) Enter the credentials of S-User or email ID mapped to SAC in step 1.7.
1.13) Set Location ID, the same value as to be used later in SAC configuration.
Step 2: Configure S/4HANA to SCC
The next step is to connect On-Premise S/4HANA to the Cloud Connector
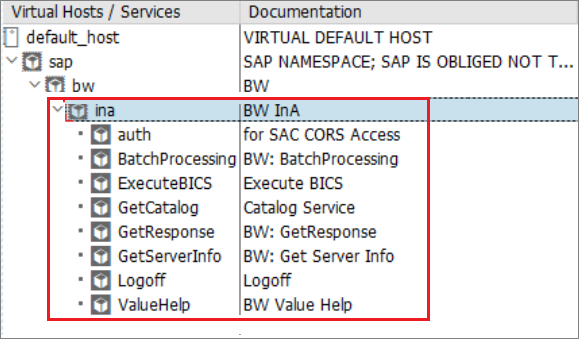
2.1) Login to S/4HANA System, execute SICF transaction.
2.2) Make sure the ICF services under the service path /sap/bc/ina are active.
2.3) Login to SAP Cloud Connector and Select the sub-account of SAC in SAP Cloud Connector.
2.4) Select Cloud to On-Premise, in the left-side menu.
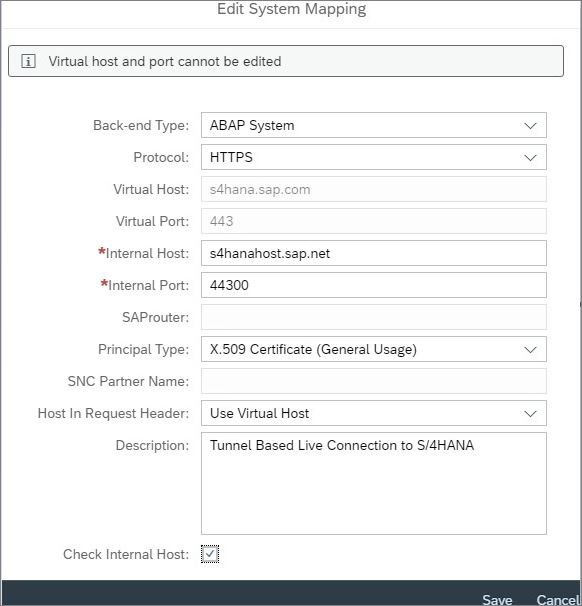
2.5) On the Access Control tab, in the Mapping Virtual to Internal System section, click +(Add) to add the On-Premise S/4HANA which serves as source for live data to SAC
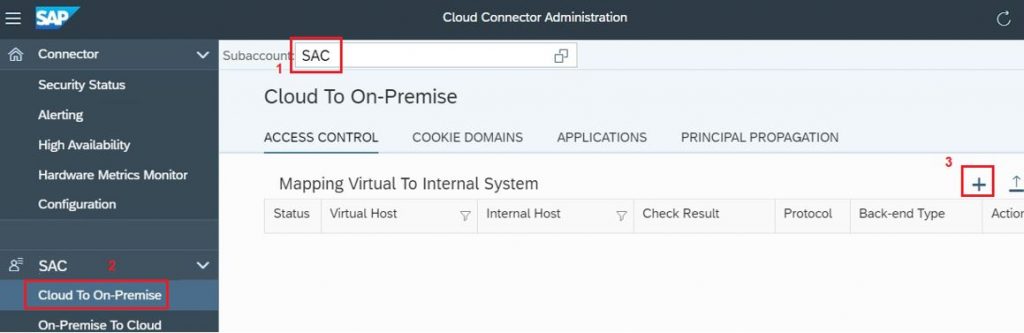
2.6) Add the below values
- Back-end system type > ABAP System for S/4HANA
- Protocol for accessing back-end system > HTTPS
- Internal host and Port of S/4HANA
- Virtual host and port defined to S/4HANA
- Propagation Principal > X.509 Certificate (General Usage) for SSO based on Tunnel connection
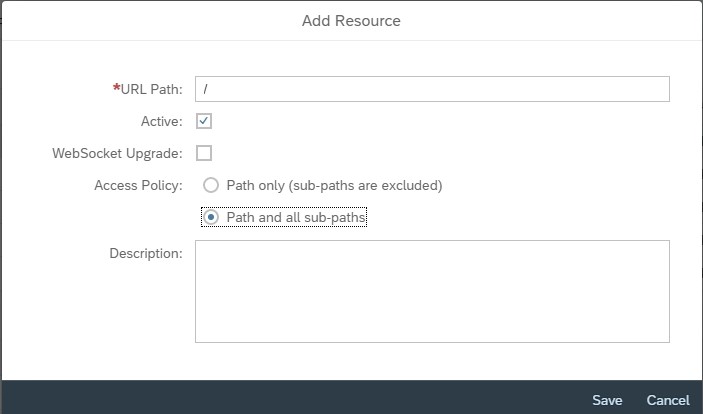
2.7) In the Resources section, Click + (Add), Enter the URL Path: “/”, Choose Path and all sub-paths and select Save, to allow access to S/4HANA system paths.
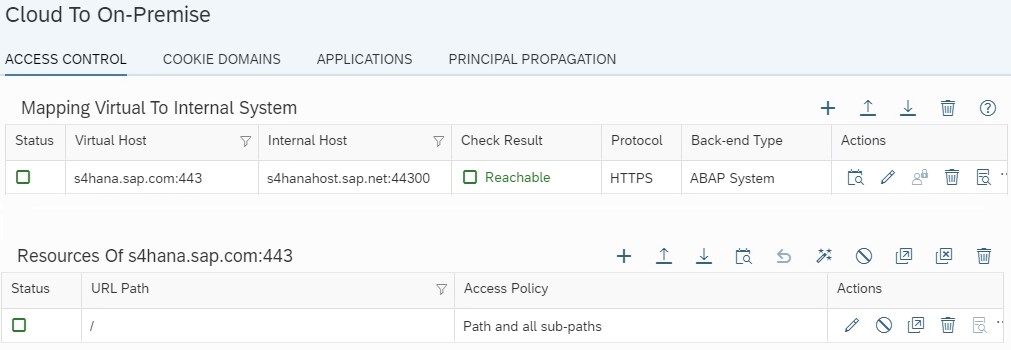
2.8) Perform connection test from SCC to make sure that the host of S/4HANA is reachable from SCC.
Note:
When the backend S/4HANA is accessed using the web dispatcher or Load Balancer, select Other SAP System as the Backend type in step 2.4. All other options (from step 2.4 to 2.6) will remain the same.
Also, when the dispatcher or the load balancer are configured to SCC, the connection test result will be Non-Reachable which can be ignored as per the SAP Note 2695217.
Step 3: Principal Propagation Configuration in SCC
SAP Cloud Connector by default does not trust any of the Identity Providers. To establish SSO using Principle Propagation, SCC must trust the Identity Provider of SAC. SCC supports the SAML2 Identity Provider to establish trust for Principal Propagation.
3.1) In the SCC Menu, Navigate to Cloud to On-Premise and go to the Principal Propagation tab.
3.2) The list of trusted identity providers is empty by default. Select the Synchronize button to synchronize the identity providers.
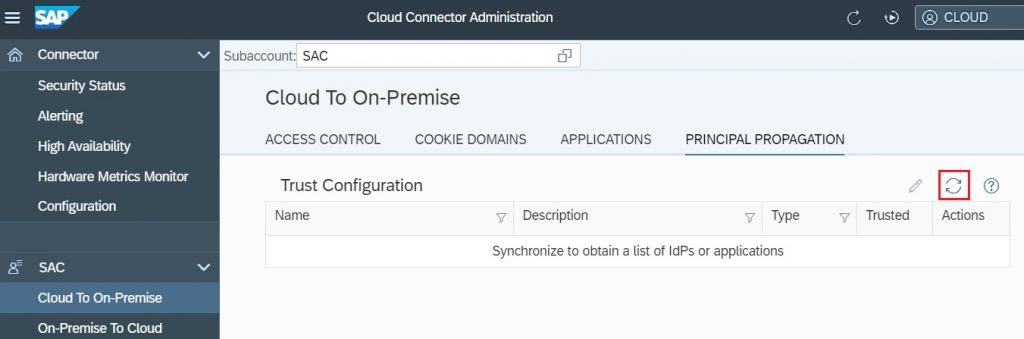
3.3) Select the Identity Provider of SAC, choose Edit, and select the Trusted checkbox.
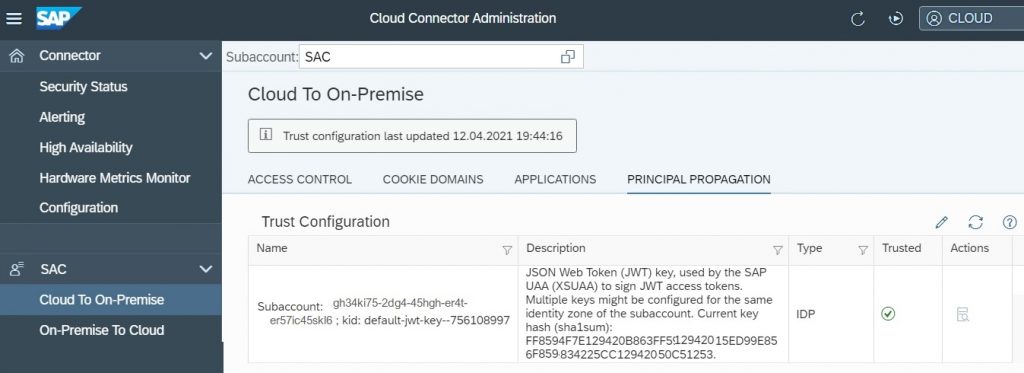
Note:
If the SAC is hosted on Non-SAP Data Centre (Cloud Foundry), where JASON Web Token (JWT) key and JWT access token are used but if SAC is hosted on NEO data center then SAML token will be used.
Step 4: Configure certificates in SCC for Principal Propagation
The SSO based on Principal Propagation between SAC and S/4HANA requires the below listed certificates:
SCC System Certificate: Used to represent the SCC as a system. This certificate is used to establish trust between SCC and the backend system.
SCC CA Certificate: Based on this certificate a short-lived X.509 certificate gets generated on the fly based on SAML/JWT token.
SCC Principle Propagation Certificate: It is a sample certificate based on the short-lived X.509 certificate. It has the subject pattern and the identifier to be used for authenticating user request at the backend system.
The above lists three certificates that must be generated in the SAP Cloud Connector.
4.1) Generate SCC System Certificate
The Cloud Connector uses the system certificate to establish trust for all HTTPS requests to the backend systems.
There are three options to generate the SCC System certificate:
Option 1: Generate CSR for SCC System Certificate and get it signed by Certificate Authority (CA) of the organization.
Option 2: Generate Self-Signed system certificate (applicable as of SCC version 2.10).
Option 3: Copy SCC UI certificate and Reuse it as system certificate.
In this blog we will follow the Option 1, generating SCC System Certificate.
Note: The Certificate authority used to sign the generated Cloud Connector system certificate must be trusted by all backend systems to which the Cloud Connector is supposed to connect. It is recommended to sign the SCC System CSR using Certificate Authority which is used to sign the CSR of the backend system.
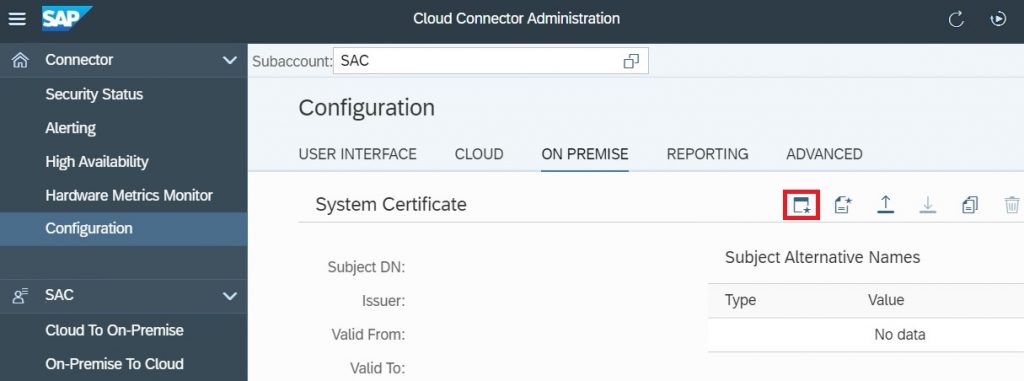
4.1.1) In SAP Cloud Connector, Navigate to Configuration menu in SCC. Click the On Premise tab, select Generate Certificate Signing Request (CSR) button in System Certificate section.
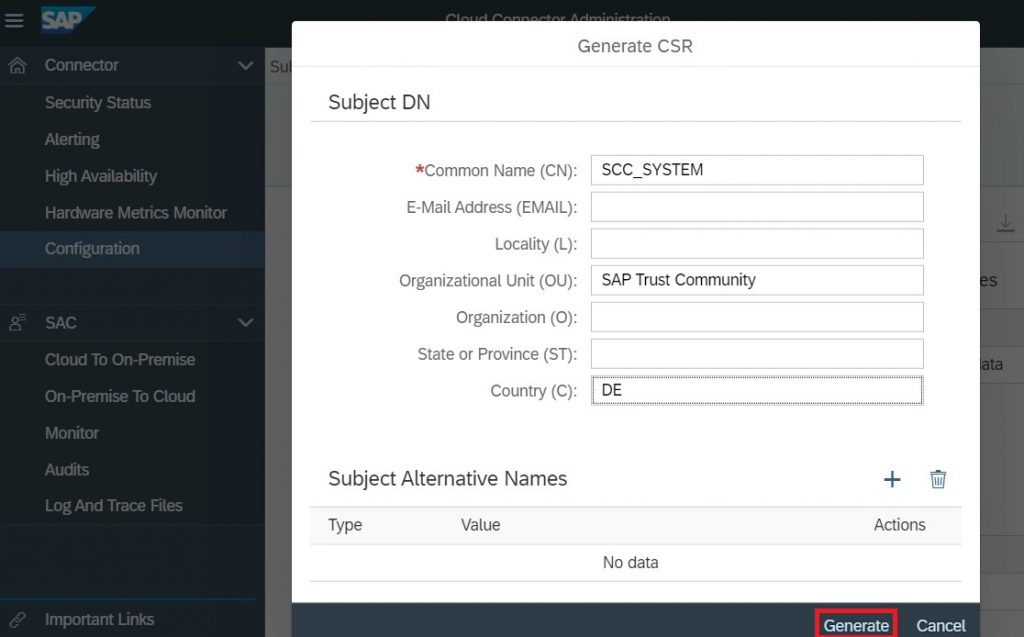
4.1.2) Upgrade the value of CN, OU and C for System certificate, click Generate. The CSR gets downloaded.
4.1.3) Sign the CSR using Certificate Authority, Upload the signed CSR in SCC system certificate section.
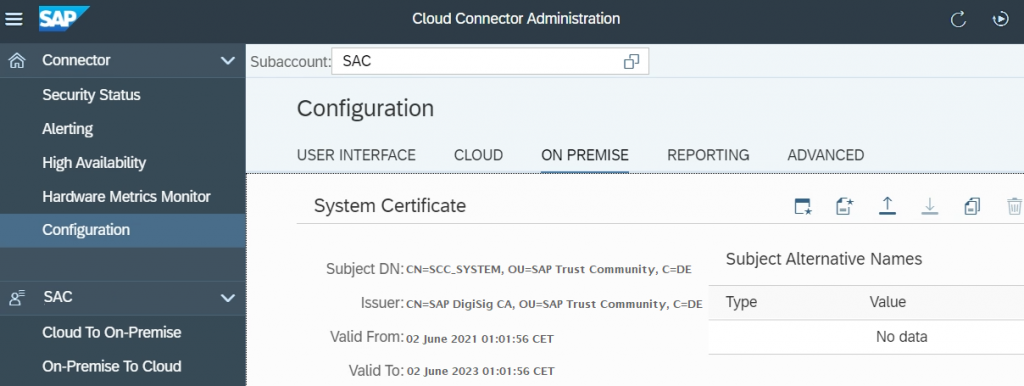
4.1.4) Download the SCC System Certificate to the local system. This certificate is used to establish trust with the backend system.
4.2) Generate SCC CA Certificate
The SSO between SAC and the backend system is based on short-lived X.509 certificate issued by the SCC CA certificate, which is used for Principal Propagation to a back-end system.
There are three options to generate the SCC System certificate:
Option 1: Import PKCS#12 certificate file from the file system.
Option 2: Generate CSR for SCC Local CA certificate and get it signed by CA of the organization.
Option 3: Use Self-signed system certificate (Applicable as of SCC version 2.10).
In this blog we will follow the Option 2, generating SCC Local CA Certificate.
Note: The Certificate Authority used to sign the Cloud Connector CA certificate must be trusted by all backend systems to which the Cloud Connector is supposed to connect. It is recommended to sign the SCC CA CSR using Certificate Authority which is used to sign the CSR of the backend system.
4.2.1) In SAP Cloud Connector, Navigate to Configuration menu, Click the On-Premise tab, select the Generate Certificate Signing Request (CSR) button in CA Certificate section.
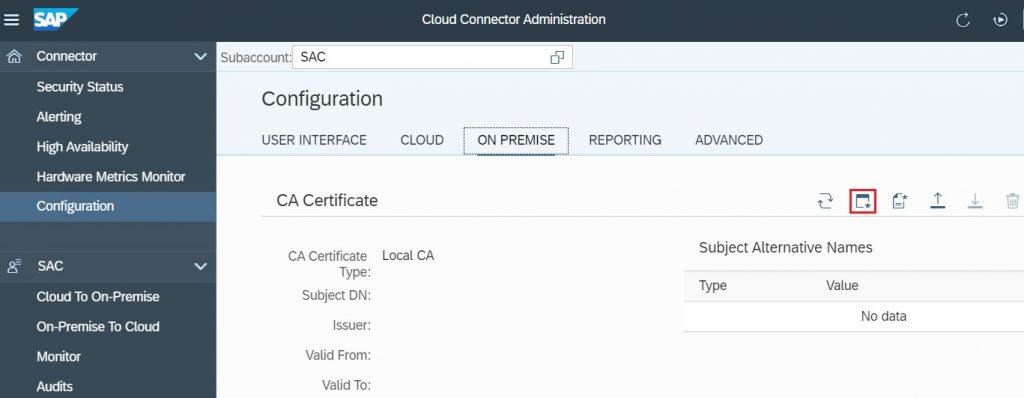
4.2.2) Upgrade the value of CN, OU and C for SCC Local CA certificate, Click Generate.
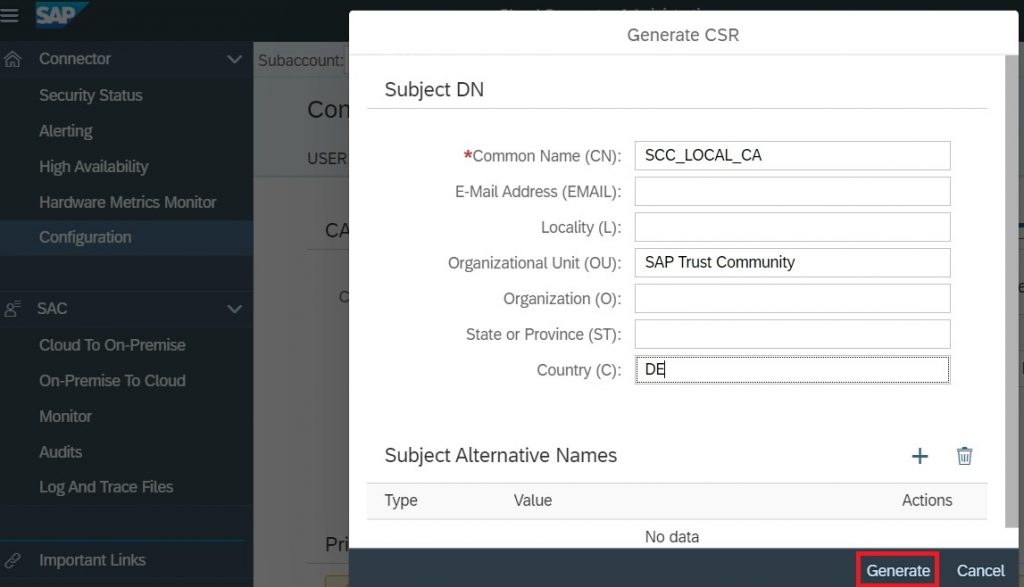
4.2.3) Sign the CSR using Certificate Authority, Upload the signed CSR in SCC CA certificate section.
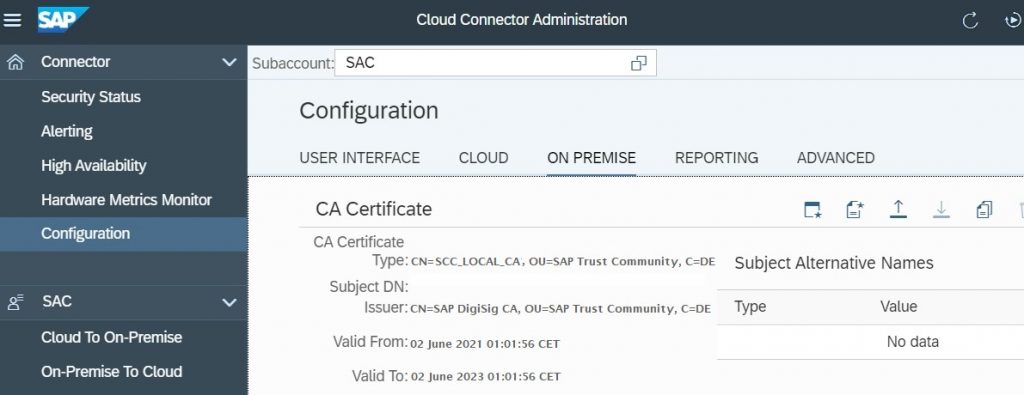
Note: The CSR generated for CA certificate will have the KeyUsage attribute keyCertSign. The certificate is signed by Certificate Authority must have the key usage attribute keyCertSign.
4.2.4) If the CSR signed by CA does not have the KeyUsage attribute keyCertSign, it will lead to the error “CA Certificate is missing KEYCERTSIGN property”.
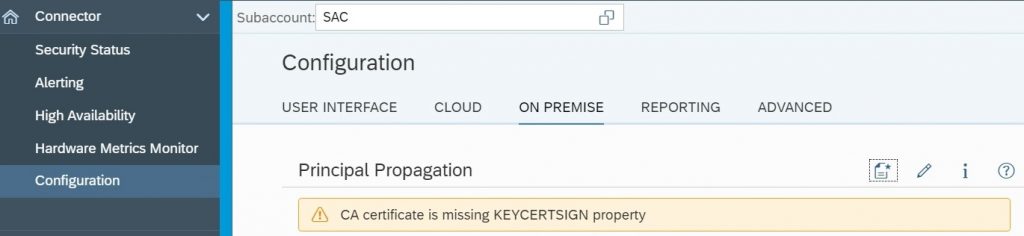
As per the SAP Note 2054122, even if Certificate Authority is not able to add the keyCertSign attribute to CSR, the SAP Systems will accept and recognize the certificate form Cloud Connector and these warnings can be ignored.
But many systems check for the KeyCertSign attribute in the certificate and deny a connection request without this attribute.
4.3) SCC certificate for Principal Propagation
The certificate for Principle Propagation is a sample certificate based on (or looks like) the short-lived X.509 certificates created at runtime. This certificate is used to create user mapping rules in the target system.
The identifier defined in the subject pattern of the sample certificate can be the user ID or email ID which gets propagated through the X.509 short-lived certificate, and a connection request is authenticated at backed based on this identifier.
4.3.1) In SAP Cloud Connector, Navigate to Configuration menu in SCC. Click the On-Premise tab, scroll down to Principal Propagation section.
4.3.2) In the Subject Pattern field, the value of Common Name is set as CN=${Name} and select Generate Sample Certificate.
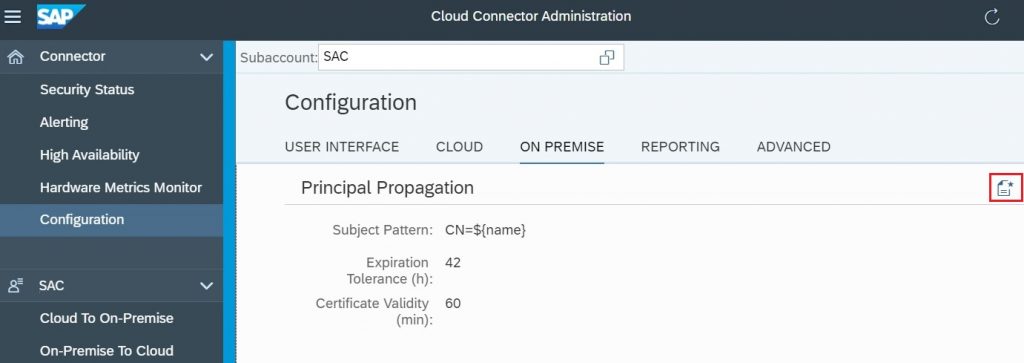
4.3.3) Define the sample value to the Common Name field (CN Name). In this scenario the email ID is used as identifier for authentication between identity provider and the SAP backend system, hence the email ID is defined as the sample value.
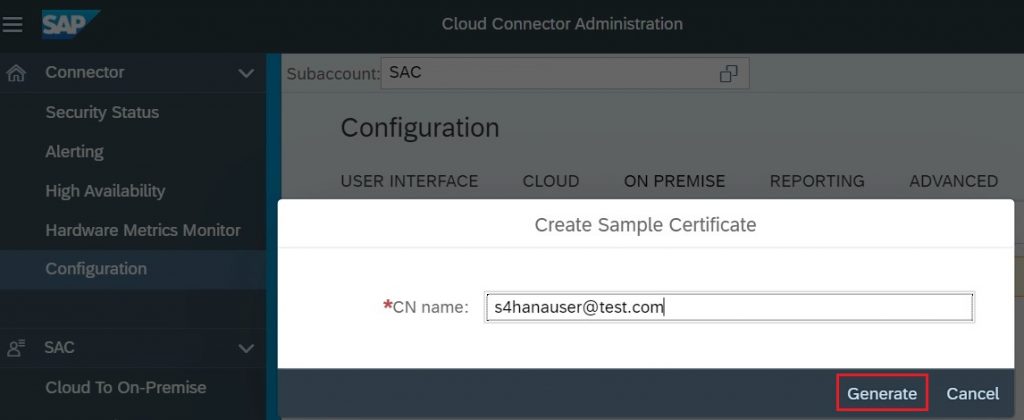
4.3.4) Click Generate to download the certificate to the local system.
Note: Make sure the backend system has SAP user with this email ID mapped to it.
Step 5: Setup trust between SCC and web Dispatcher
This step is applicable only when there is an intermediate SAP Web Dispatcher between SAP Cloud Connector and S/4HANA backend system. Follow the below steps to establish trust between Cloud Connector and SAP Web Dispatcher.
In order to trust the request from SAP Cloud Connector, import the SCC system certificate to SAP Web Dispatcher.
5.1) Login to Web dispatcher with Admin user.
5.2) In the menu, navigate to SSL and Trust Configuration and select PSE Management.
5.3) In the Manage PSE section, select SAPSSLS.pse from the drop-down list.
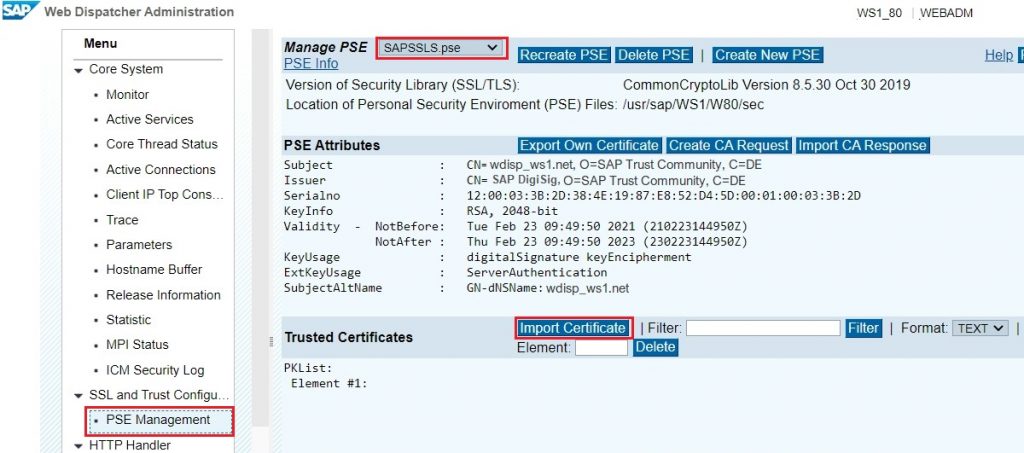
5.4) In the Trusted Certificates section, choose Import Certificate, Select the local copy of SCC System Certificate generated in step number 4.1.4.
5.5) Choose Import. The certificate details are now shown in the Trusted Certificates section.
By default, SAPSSLS.pse of Web dispatcher contains the server certificate of trusted clients and the Web Dispatcher trusts the requests from those clients.
5.6) Add the below listed parameter to the Web Dispatcher instance profile to trust the Cloud Connector system certificate for Principal Propagation.
5.6.1) Set icm/HTTPS/verify_client=1. The default value of the parameter icm/HTTPS/verify_client is 1, so it is fine even if the parameter is not defined in the system.
5.6.2) Set icm/trusted_reverse_proxy_<x> = SUBJECT=”< Subject of the SCC system certificate >”, ISSUER=”< Issuer of the system certificate >”
E.g.: icm/trusted_reverse_proxy_0= SUBJECT=”CN=SCC_SYSTEM, O= SAP Trust Community, C=DE”, ISSUER=”CN=SAP DigiSig CA, O= SAP Trust Community, C=DE”.
Hint: The value of Subject and Issuer can be found in the Cloud Connector application > Configuration Menu > On-Premise tab > System Certificate section.
During the initial run define the value of SUBJECT and ISSUER as “*”. Once the connection is successful you can define the respective values of subject and issuer of the SCC certificate.
Note: The parameter icm/HTTPS/trust_client_with_issuer and icm/HTTPS/trust_client_with_subject has been deprecated by SAP and it is recommended to use icm/trusted_reverse_proxy_<x>.
5.6.3) Set icm/HTTPS/forward_ccert_as_header=TRUE
5.7) Restart the web dispatcher to activate the parameter changes.
Step 6: Setup Trust between SCC and On-Premise S/4HANA
The On-Premise S/4HANA system must be configured to accept and trust the short-lived X.509 certificate from the cloud connector. The SSO based on Principle Propagation is used for authenticating the request at S/4HANA.
Note: To configure Single Sign-On using Principal Propagation between SAC and S/4HANA, both SAC and S/4HANA must be configured to the same Identity Provider (IdP).
To enable custom Identity Provider in SAP S/4HANA, Please follow the steps given in this Official guide for Custom IdP Configuration in S/4HANA.
Follow the below steps to establish trust between SCC and S/4HANA:
6.1) Login to S/4HANA system, execute transaction STRUST.
6.2) Select the Server Standard Certificate to import the SCC System Certificate generated in section 4.1.4.
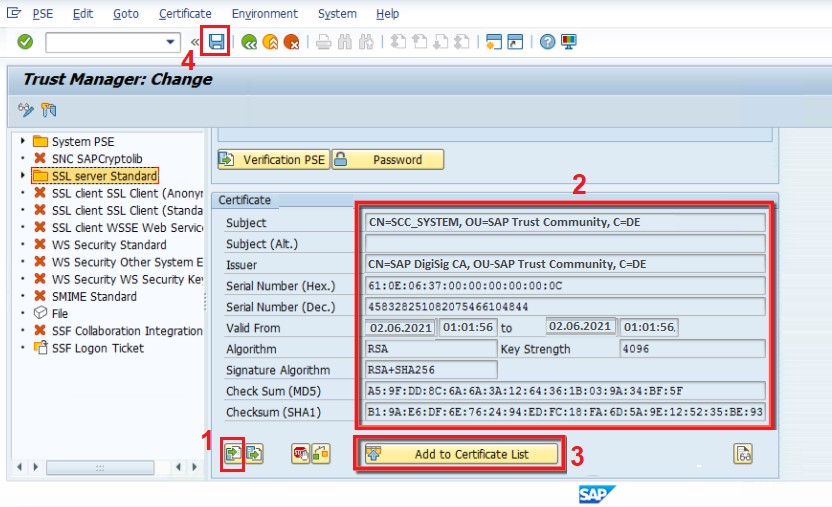
6.3) Click Add to Certificate List button and Save the transaction.
6.4) Execute the RZ10 transaction. Add the below listed parameters to the default profile to trust the Cloud Connector system certificate for Principal Propagation.
6.4.1) Set icm/HTTPS/verify_client=1
6.4.2) Set icm/trusted_reverse_proxy_<x> = SUBJECT=”< Subject of the SCC system certificate >”, ISSUER=”< Issuer of the system certificate >”
E.g. icm/trusted_reverse_proxy_0= SUBJECT=”CN=SCC_SYSTEM, O= SAP Trust Community, C=DE “, ISSUER=” CN=SAP DigiSig CA, O= SAP Trust Community, C=DE”.
During the initial run define the value of SUBJECT and ISSUER as “*”. Once the connection is successful you can define the respective values of subject and issuer of the SCC certificate.
6.4.3) Set login/certificate_mapping_rulebased=1. This parameter enables to map the short-lived certificate to S/4HANA.
6.5) Restart the application server to activate the parameter changes.
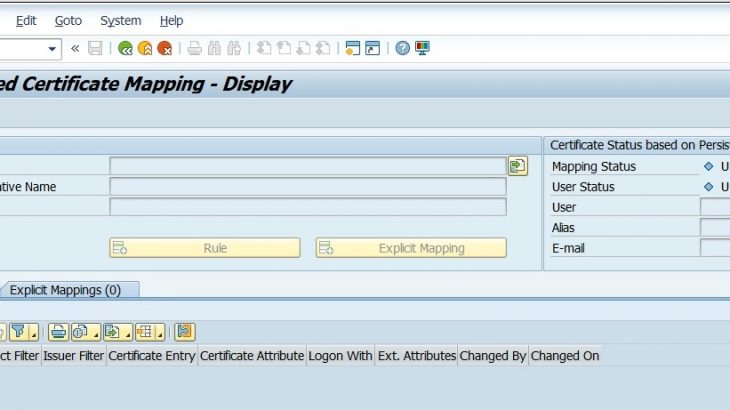
6.6) Execute the transaction CERTRULE (Rule based Certificate Mapping) for mapping short-lived certificate to S/4HANA.
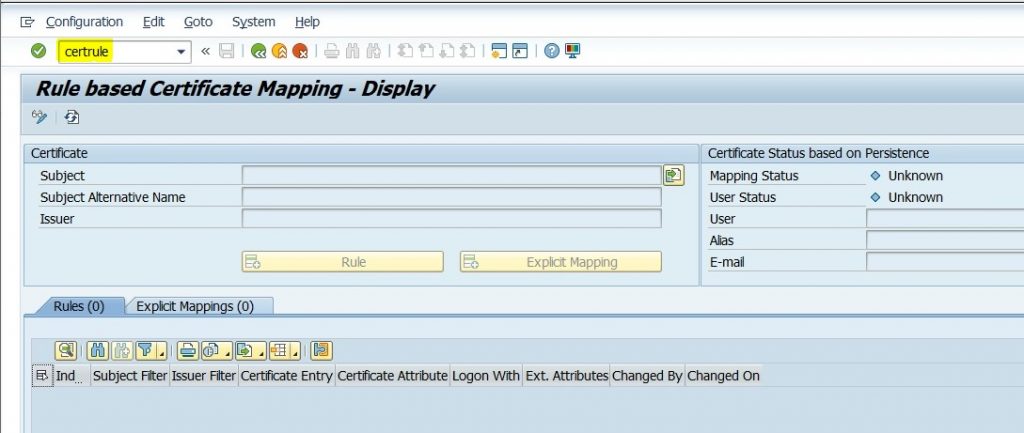
6.7) Click on Change, In the Menu Bar Navigate to Configuration > Upload certificate.
6.8) Choose the sample Principle Propagation certificate file that was previously generated from the Cloud Connector in section 4.3.4 (not the SCC system certificate file).
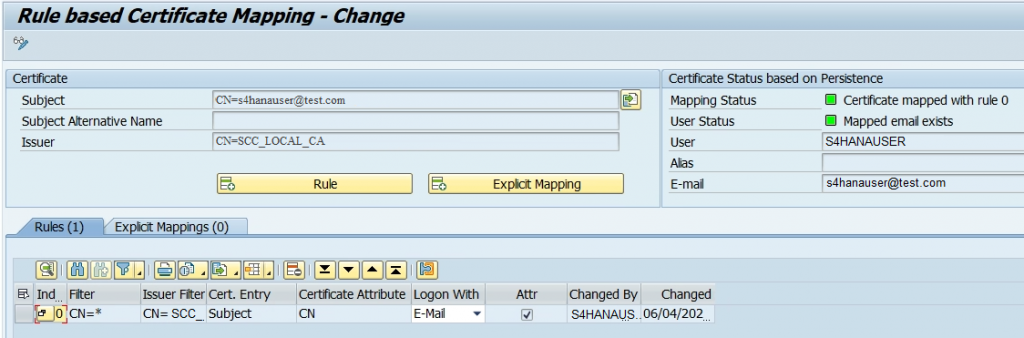
6.9) When the sample certificate is loaded in S/4HANA, the CN value of SCC Local CA and identifier gets populated in the screen.
The Mapping status remains in Red indicating the message Certificate is not mapped.
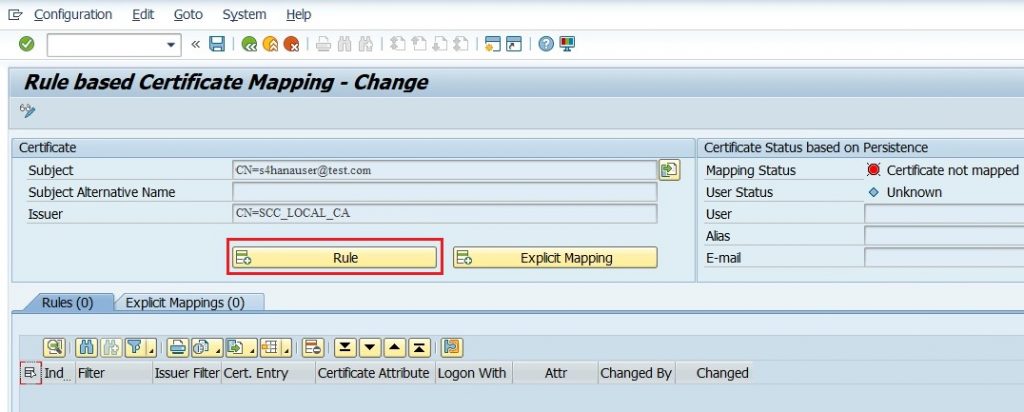
6.10) Select the Rule button to create a new rule.
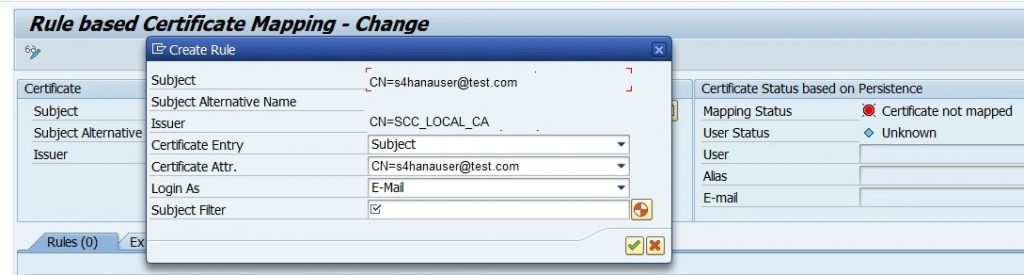
6.11) In the Create Rule screen, define the identifier (email ID) that was used while generating the sample certificate in the step 4.3.3.
6.12) In Login As field, choose email ID from dropdown and in the Certificate Attribute field, select the email from the drop down menu. Click the tick mark to proceed further.
6.13) In the next screen click the Attribute and select the Ignore case sensitivity in certificate entries.
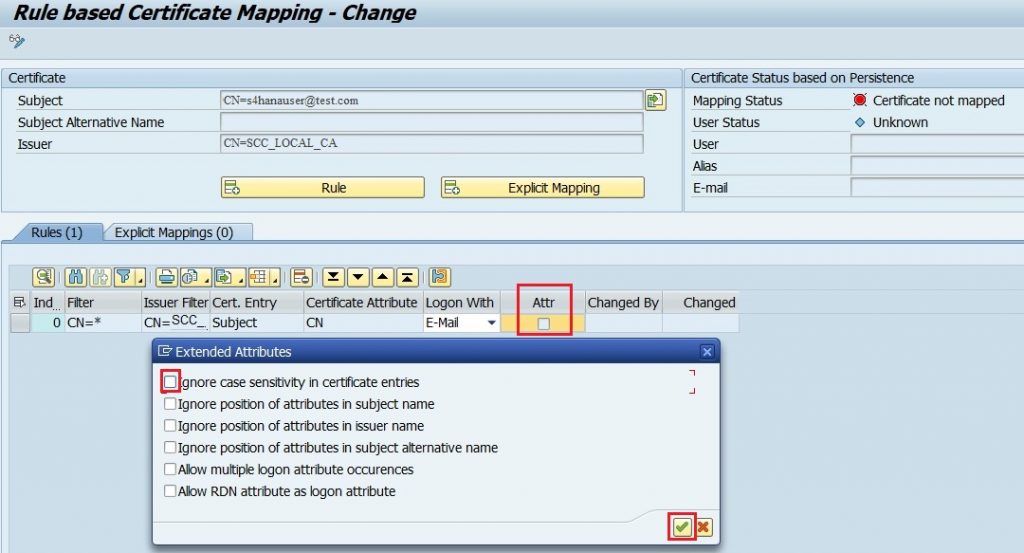
6.14) Click Save button. The Mapping Status turns green and displays the associated S/4HANA user when the email id of the sample certificate is validated against the user in S/4HANA.
Step 7: Configure Tunnel Live Data Connections in SAC
Follow the below steps to create the live data connection between SAP Analytics Cloud and S/4HANA using Tunnel Connection via SAP Cloud Connector.
Note: To configure Single Sign-On between SAC and S/4HANA, make sure both SAC and S/4HANA must be configured to the same Identity Provider (IdP).
7.1) Login to SAC as an Administrator.
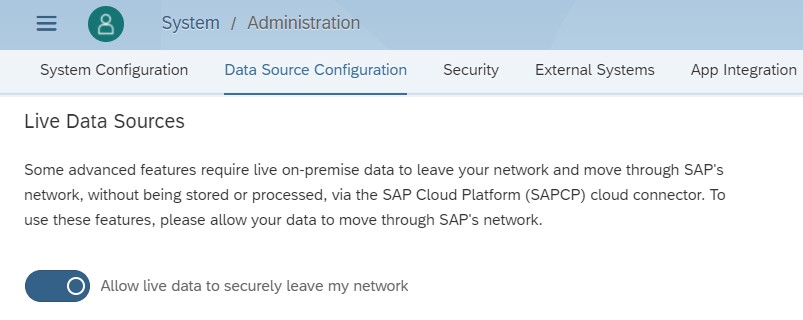
7.2) Navigate to Main Menu > System Administration > Data Source Configuration.
7.3) Enable toggle button Allow Live Data to securely leave my network. This has to be enabled in order to use the SCC tunnel in a SAC live data connection.
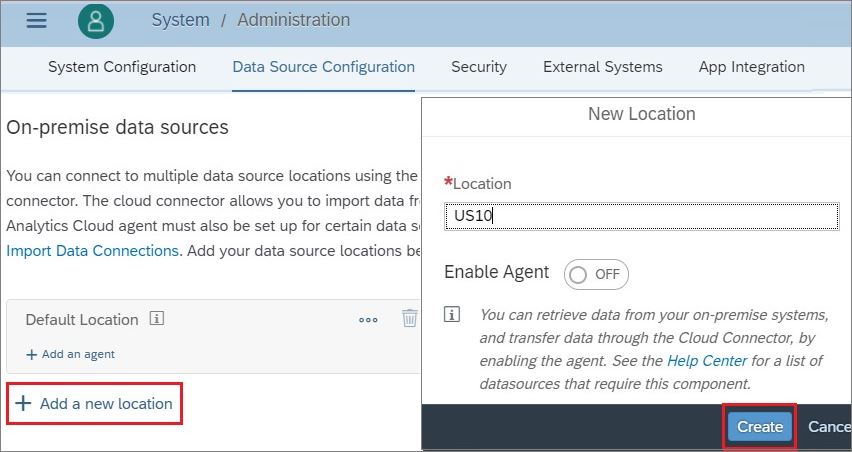
7.4) In the next section click Add a New Location and enter the location ID defined while configuring SAC to SCC in step 1.13. In this example I have defined it as US10, click Create and Save the configuration.
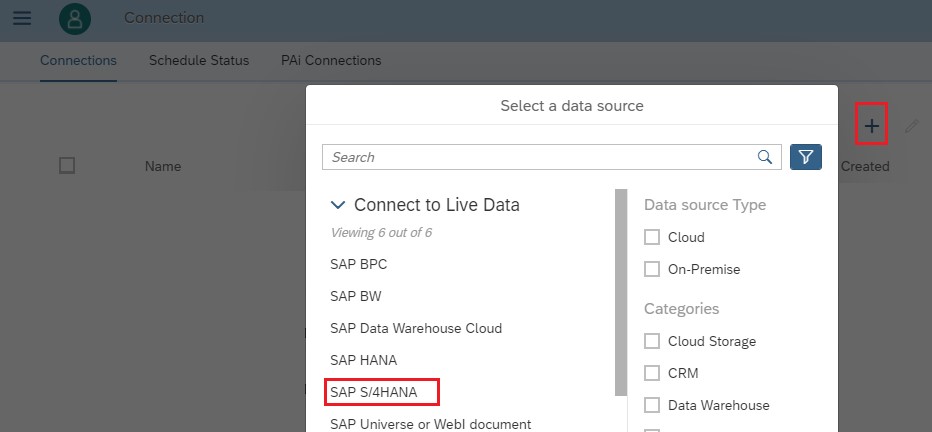
7.5) Navigate to the Main Menu > Connection > Click the + button to create new connection and select S/4HANA.
7.6) In the pop-up screen, provide the following details to setup Tunnel live connection between SAC and S/4HANA with SSO.
- Name : <Name of Live Connection> Eg TUNNELCONN
- Description: Description to Live Connection
- Connection Type : Tunnel
- Location ID: Location ID mapped to SAC In Step 7.4
- Host : Virtual Host Name of S/4HANA or Webdispatcher in SCC
- Port: Virtual Port number configured in SCC
- Authentication Type: SAML Single Sign-on
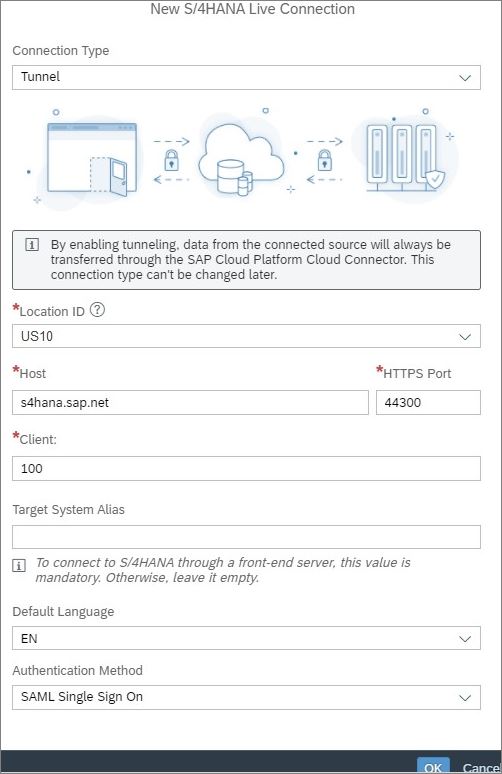
7.7) Click OK to create connection to S/4HANA.