Introduction
Business Process Monitoring powered by SAP Cloud ALM provides out of the box a bunch of Key Performance Indicators (KPIs) covering the end to end processes Lead to Cash, Source to Pay, Design to Operate and Recruit to Retire.
These business process indicate the health of the underlying business process, help to understand anomalies during process execution and thus ensure business continuity. It provides detailed information on business process documents and allows a centralized and unified analysis of critical situations.
It is spanning over multiple SAP products such as SAP S/4HANA Cloud, SAP S/4HANA, SAP Business Suite, SAP SuccessFactors and SAP Cloud for Customer.
Business Process Monitoring is intended for business users – focusing on specific areas, a role specific environment can be beneficial and contribute to the overall business continuity.
With Access Control we are providing you the option to grant tailored access.
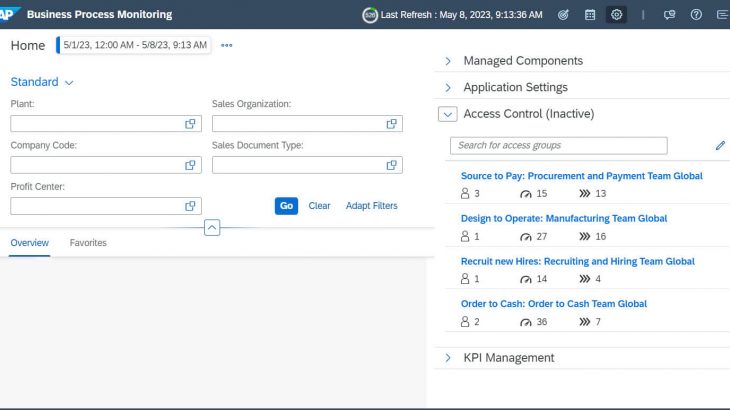
Access Control
In Access Control access groups can be defined with which you can restrict the access to authorized users for a particular business process scope.
By default, Access Control is deactivated, so all users are able to access the monitoring data for all business processes.
As a Process Monitoring Administrator, you can create access groups and, once all users are assigned to a group you can activate access control. Details can be found in section “Activating Access Control”.
In order to get to the Access Control – Launch Settings:
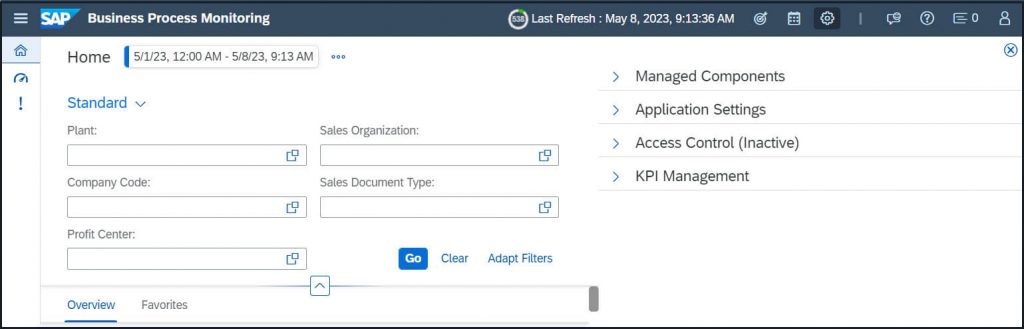
Expand Access Control Section:
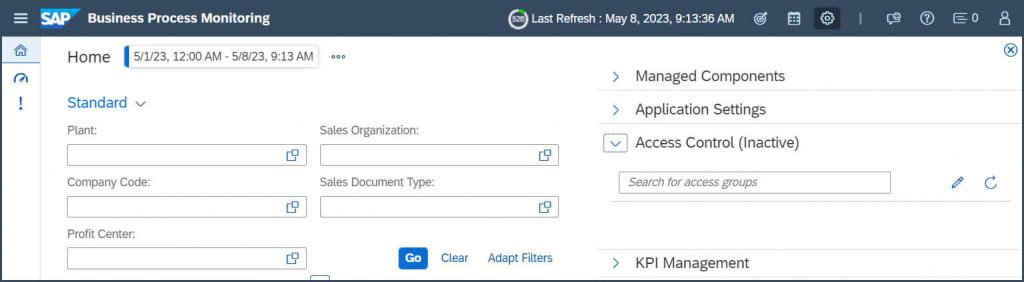
Click “Add” (+) to create a new access group:
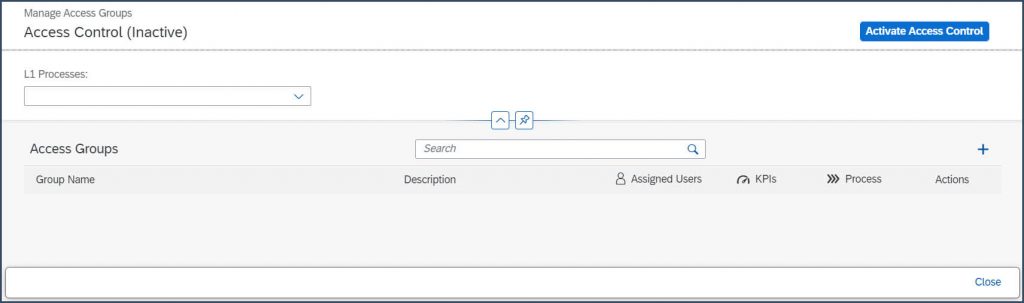
Enter a group name and description:
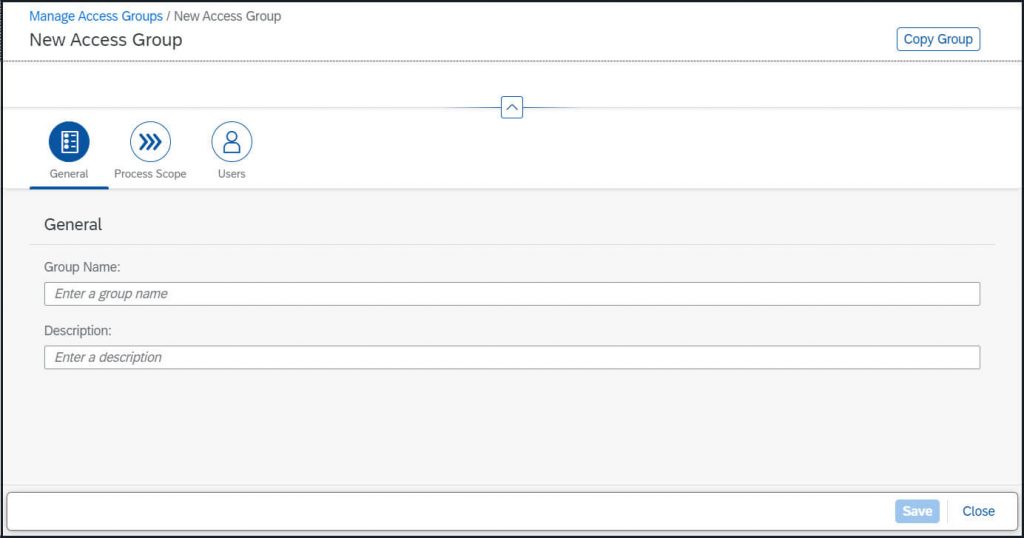
Assign Process Scope – by selection the respective process node – this can be e.g. the end-to-end process, any other process or subprocess level or a selection of various items:
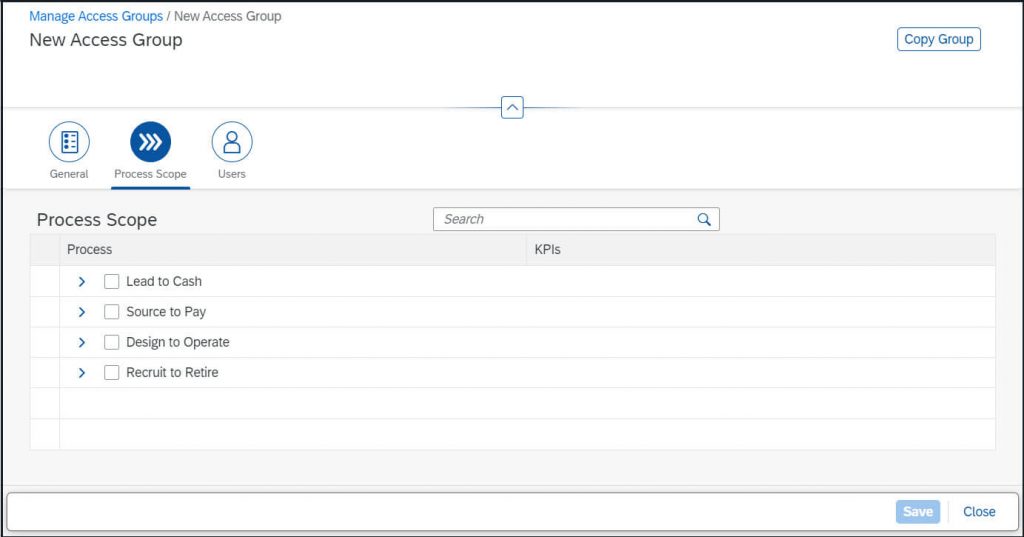
As last step you need to assign the users to the group:
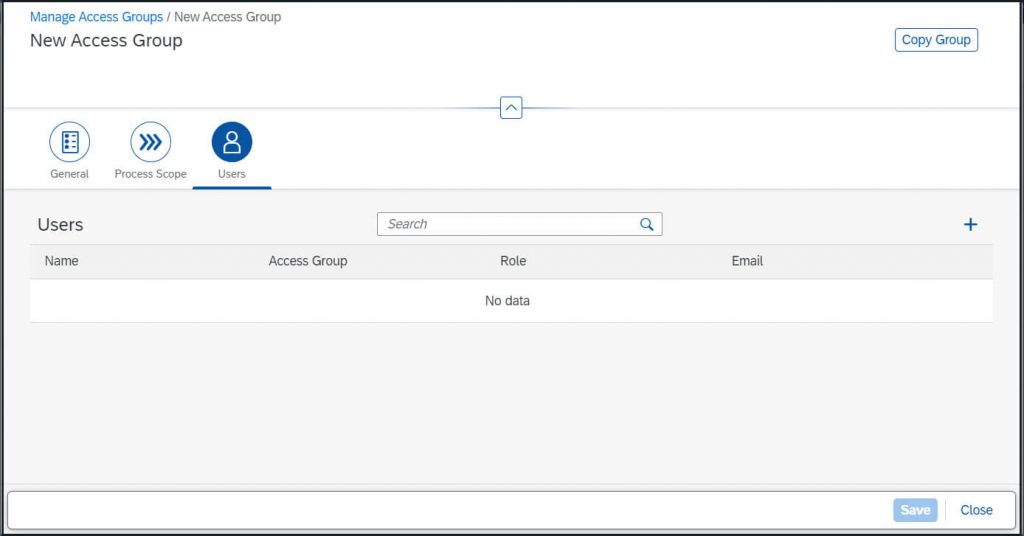
Save Changes.
Personas
To show you how access groups can be used – let me introduce you to my sample business users:
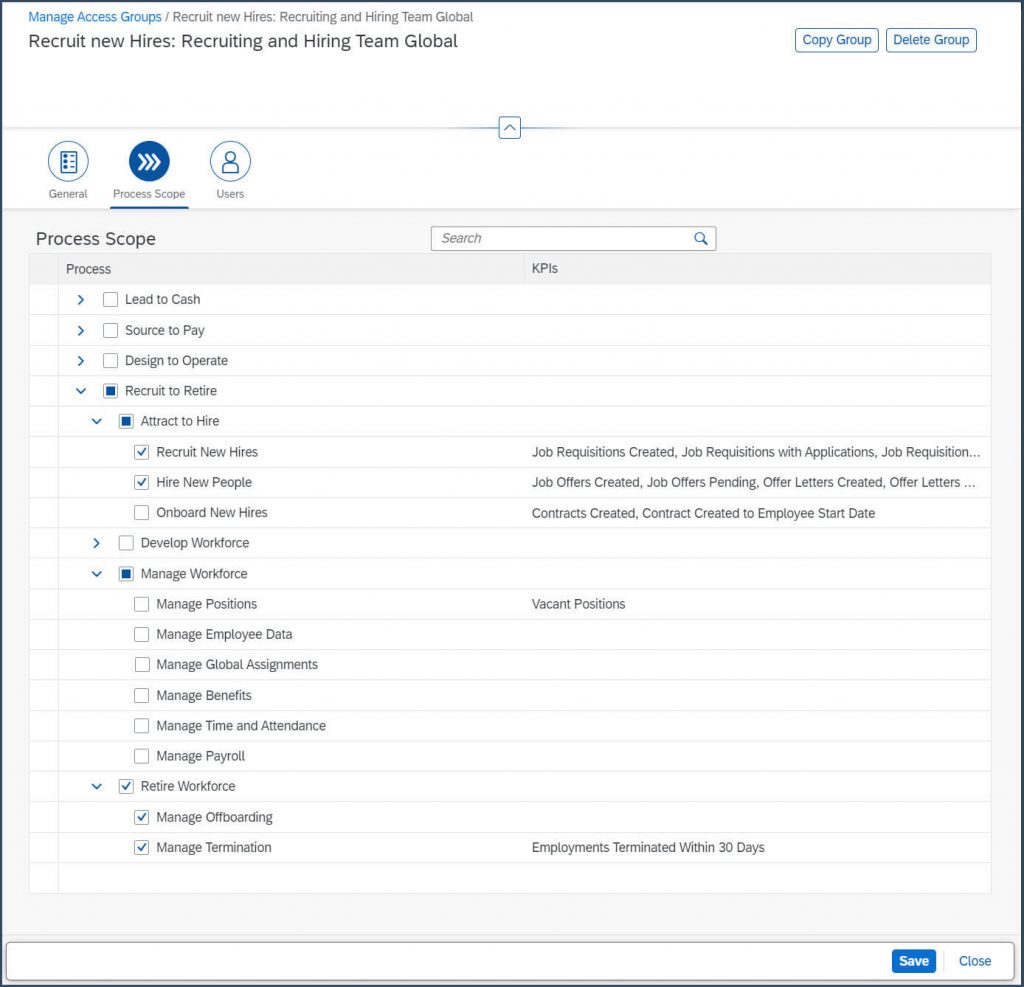
Kim is working as recruiter and is supporting the managers during the employee lifecycle from defining positions, recruiting but as well as off-boarding.
End-to-End Process: Hire to Retire
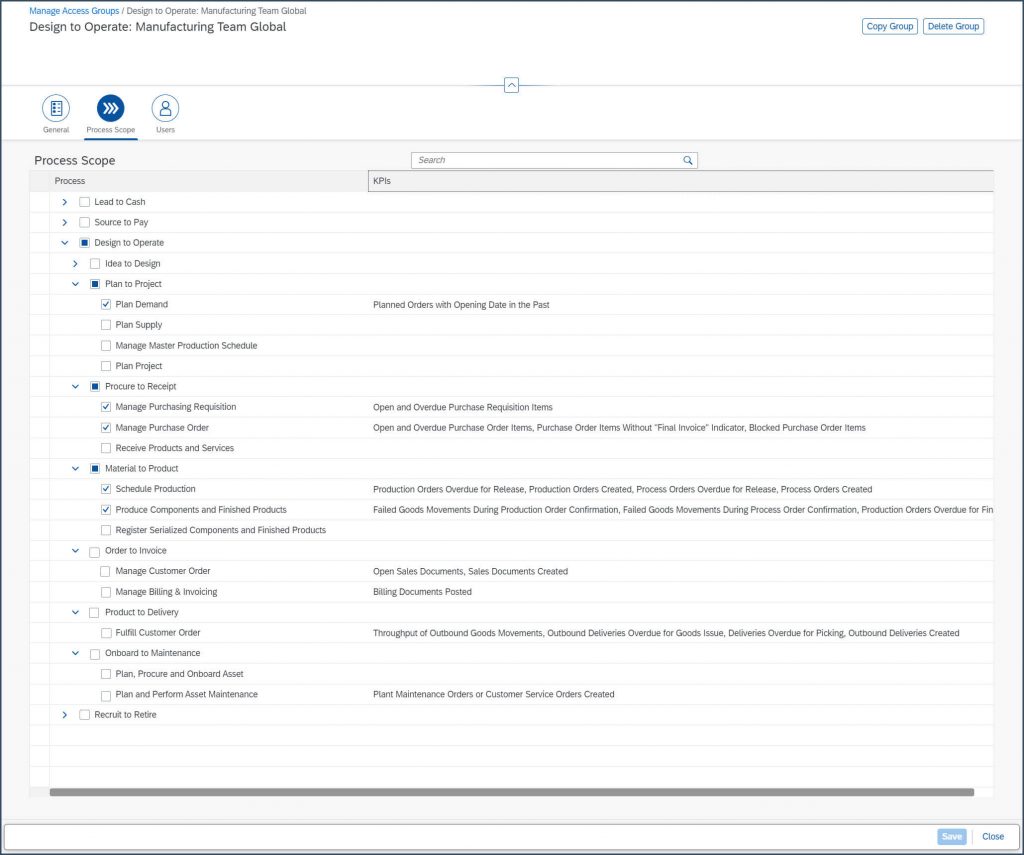
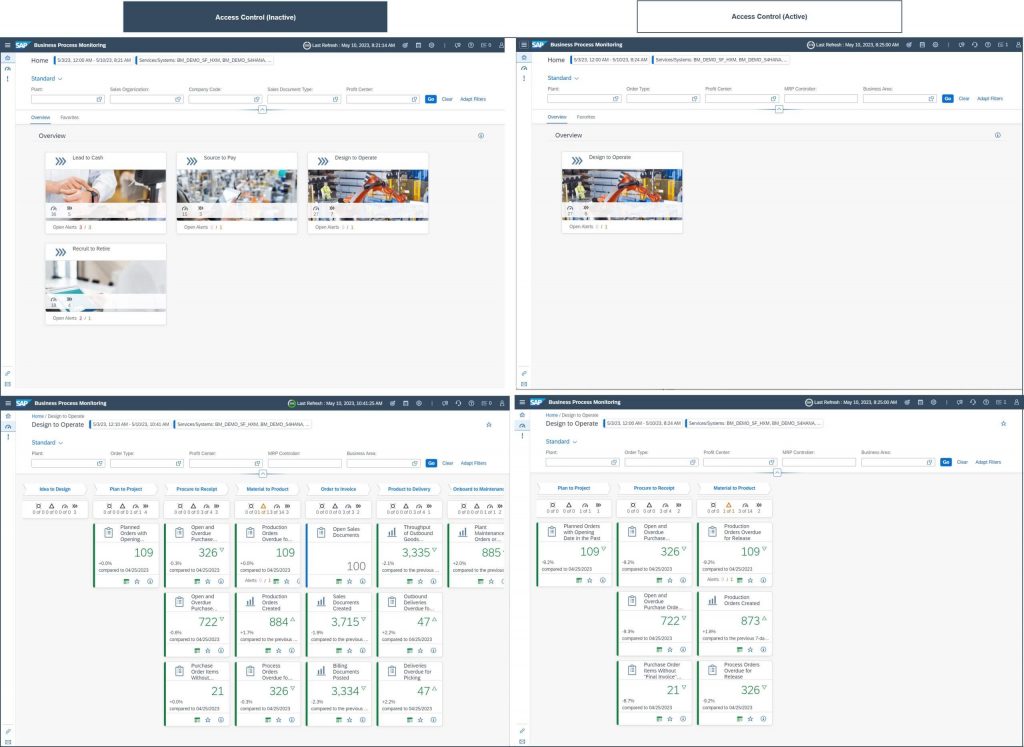
Alex is working in the Global Manufacturing Team. The team is focusing on processes Plan to Project, Procure to Receipt, Material to Product, Order to Invoice, Product to Delivery and Onboard to Maintenance.
End-to-End Process: Design to Operate
Besides personas, access control can also be used in context of restricting access: Securing information by which KPIs are visible for which user, which group of users. For example the financial department should see only Finance related KPIs – the Human Resources Team should be the only area which is using Hire-To-Retire KPIs which are powered by SAP SuccessFactors and vice versa not see the Finance content.
Activating Access Control
Once all relevant groups are defined and users are assigned to groups you can active the access control for your tenant.
Go to Settings, Open Access Control section and click on edit:
By pressing the button “Activate Access Control” – you can enable Access Control:
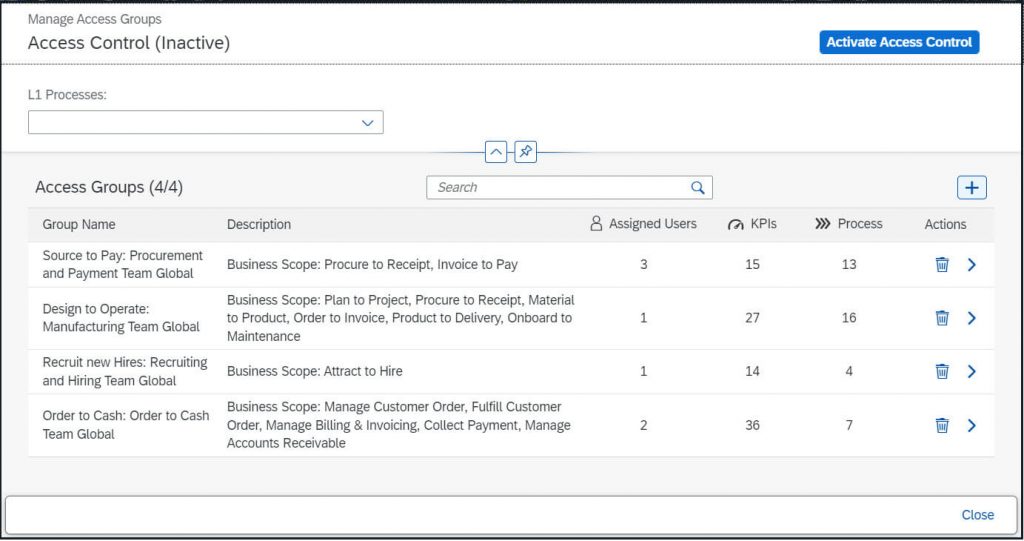
The activation can only be done and reverted by a Process Monitoring Administrator – the following information is shown during activation:
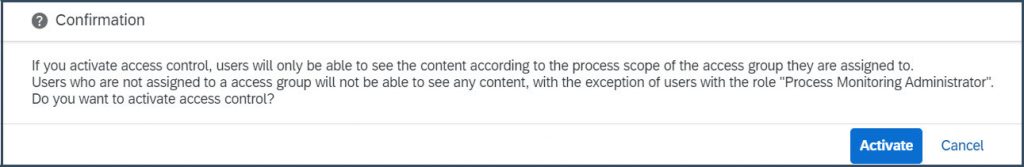
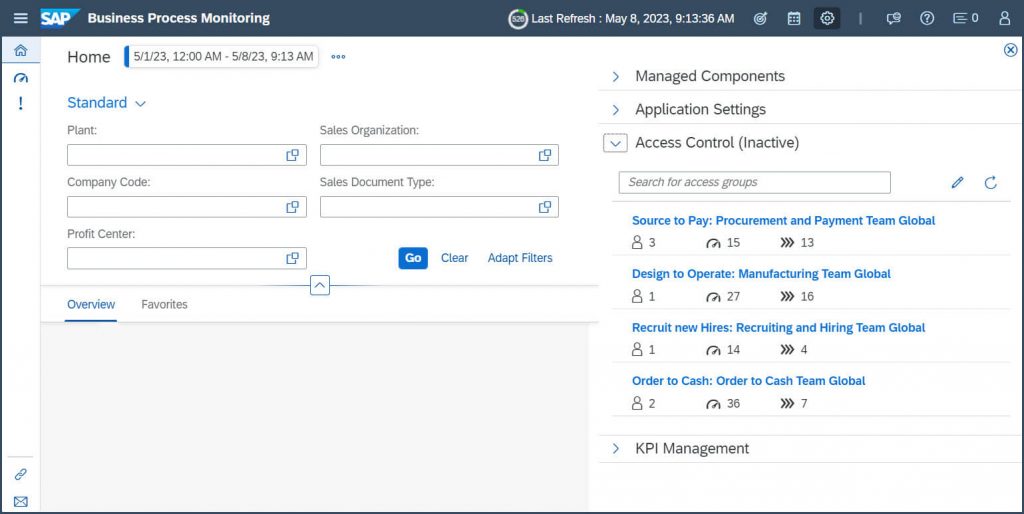
And here you can see how it looks once Access Control is active and how other access groups can look like:
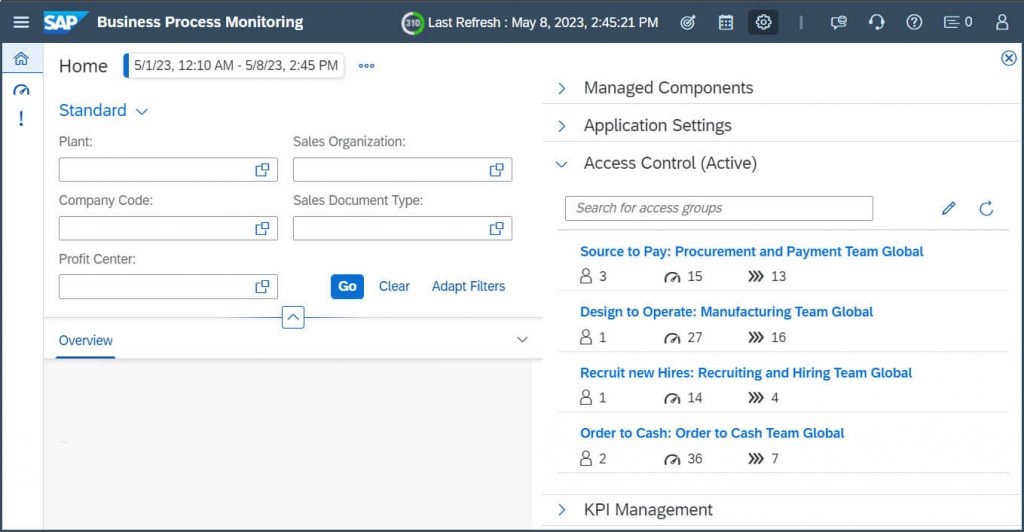
Above you can see assigned users, contained total # of KPIs and the involved processes.
Hint: In Manage Access Group area you can also use copy group to model another group with e.g. another flavor or also manage existing groups. You can check details from an existing groups – add or remove users or even delete the entire group.
Result
As as a result you can see below the details for the previously defined Personas and the respective access groups. On the left hand side you can see the application without usage of Access Control and on the right hand side how Kim is now experiencing Business Process Monitoring:
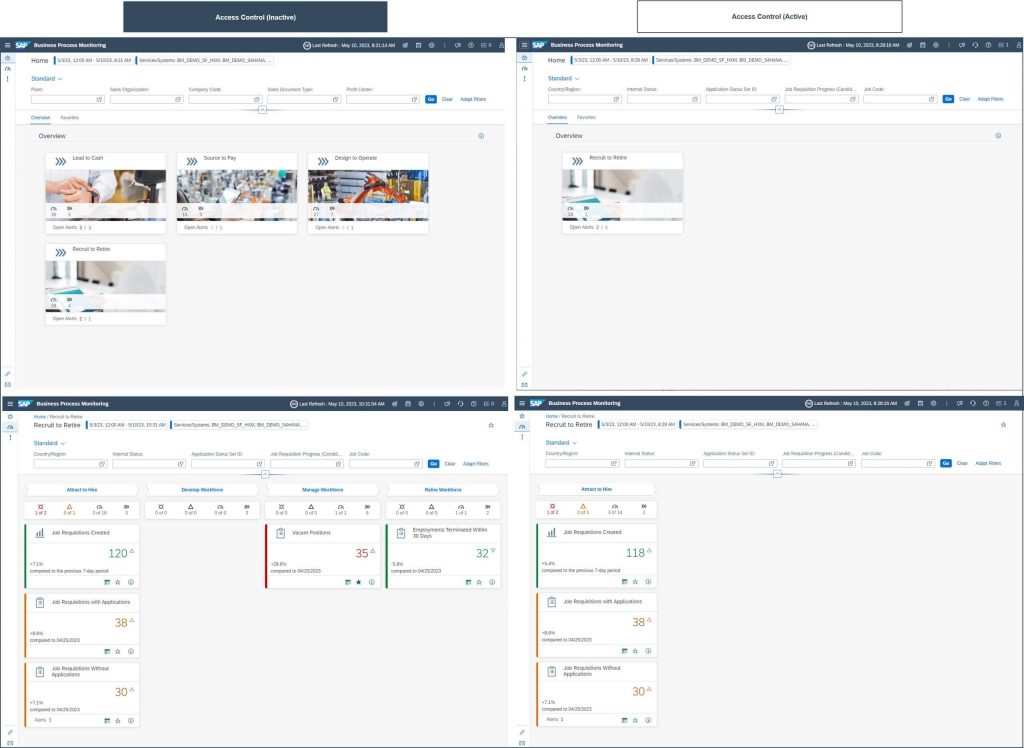
When Alex is using now Business Process Monitoring based on Access Groups. You can see on the left hand side how the application looked before and on the right hand side how business users can benefit from tailored access:
Your time
Now it is your time to start with Access Control. You can model the access groups based on what suits best for your company – for example according to processes or focus areas of key users.
You can directly now start with building groups, details are up to you, as well as when you will turn Access Control on. Make use of this tailoring option!